How To Download Anyconnect Client From Asa
In this lesson we will see how you can utilize the anyconnect client for remote admission VPN. Anyconnect is the replacement for the erstwhile Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers 2 SSL VPN modes:
- Clientless WebVPN
- AnyConnect VPN
The clientless WebVPN method does non require a VPN client to exist installed on the user's computer. Yous merely open your web browser, enter the IP address of the ASA and you will get access through a spider web portal. Y'all only have limited admission to a number of applications, for example:
- Internal websites (HTTP and HTTPS)
- Spider web applications
- Windows file shares
- Email servers (POP3, IMAP, SMTP)
- Microsoft Outlook Web Access
There is no full network admission when you use clientless WebVPN.
Anyconnect VPN offers full network access. The remote user will apply the anyconnect client to connect to the ASA and will receive an IP address from a VPN pool, allowing full access to the network.
In this lesson we will use clientless WebVPN simply for the installation of the anyconnect VPN client. The remote user will open a web browser, enters the IP address of the ASA and and so information technology will automatically download the anyconnect VPN customer and establishes the connection. Hither'due south the topology that we volition use:
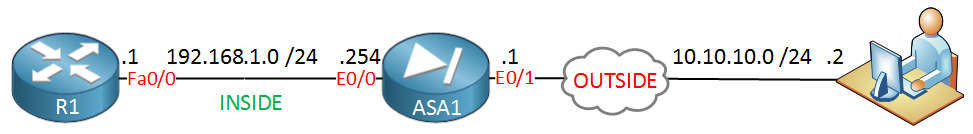
Above we take the ASA firewall with two security zones: inside and outside. The remote user is located somewhere on the outside and wants remote access with the Anyconnect VPN client. R1 on the left side will just exist used so that we can test if the remote user has access to the network. Let's take a look at the configuration!
ASA Configuration
The remote user will be able to download the anyconnect VPN client from the ASA so nosotros need to store it somewhere. Each operating system has a different installation file and we need to accept them on the flash memory of the ASA:
ASA1# evidence flash: --#-- --length-- -----date/time------ path 10 8192 December 02 2014 19:09:34 log xviii 8192 Dec 02 2014 19:09:44 crypto_archive 106 25088760 Aug 04 2014 13:59:20 asdm-731.bin 109 27113472 Aug 25 2014 thirteen:10:56 asa915-k8.bin 112 31522773 Aug 09 2014 15:01:52 anyconnect-win-3.i.03103-k9.pkg 113 9993060 Aug 09 2014 15:06:50 anyconnect-linux-3.ane.03103-k9.pkg 114 11293375 Aug 09 2014 15:08:34 anyconnect-macosx-i386-3.1.03103-k9.pkg 255426560 bytes full (149487616 bytes free) In that location is a different PKG file for each operating system. To a higher place you can run across that I have ane for Windows, Linux and Mac OS X. If y'all don't have them already, make sure you re-create them to the flash memory of the ASA.
Our adjacent step is to enable clientless WebVPN:
ASA1(config)# webvpn Now we specify which anyconnect PKG files we want to use:
ASA1(config-webvpn)# anyconnect prototype flash:/anyconnect-win-3.ane.03103-k9.pkg I'm merely specifying the anyconnect client for Windows but if yous desire to support Linux or Mac Os X users, make sure to add them hither. Now nosotros can enable client WebVPN on the outside interface:
ASA1(config-webvpn)# enable outside INFO: WebVPN and DTLS are enabled on 'Exterior'. This enables WebVPN on the exterior interface. We also need to enable anyconnect:
ASA1(config-webvpn)# anyconnect enable When you accept an inbound access-listing on the exterior interface so all your decrypted traffic from the SSL WebVPN has to match the entering access-list. You tin can either create some let statements for the decrypted traffic or you tin can just tell the ASA to let this traffic bypass the access-listing:
ASA1(config)# sysopt connection permit-vpn When remote users connect to our WebVPN they have to use HTTPS. The post-obit option is not required simply useful, whenever someone accesses the ASA through HTTP and then they will be redirected to HTTPS:
ASA1(config)# http redirect OUTSIDE 80 The ASA will assign IP addresses to all remote users that connect with the anyconnect VPN customer. We'll configure a pool with IP addresses for this:
ASA1(config)# ip local pool VPN_POOL 192.168.10.100-192.168.10.200 mask 255.255.255.0 Remote users will become an IP address from the pool above, nosotros'll use IP accost range 192.168.ten.100 – 200.
By default all traffic will be sent through the tunnel once the remote user is connected. If y'all want to allow remote users to admission the Internet one time they are connected then you lot need to configure split tunneling. We will configure an access-list that specifies what networks we desire to reach through the tunnel:
ASA1(config)# access-list SPLIT_TUNNEL standard allow 192.168.1.0 255.255.255.0 This means that the SSL VPN tunnel volition merely exist used to reach the 192.168.1.0 /24 network. At present nosotros tin configure the anyconnect group policy:
ASA1(config)# grouping-policy ANYCONNECT_POLICY internal ASA1(config)# group-policy ANYCONNECT_POLICY attributes ASA1(config-group-policy)# vpn-tunnel-protocol ssl-client ssl-clientless ASA1(config-group-policy)# dissever-tunnel-policy tunnelspecified ASA1(config-grouping-policy)# separate-tunnel-network-list value SPLIT_TUNNEL ASA1(config-group-policy)# dns-server value eight.8.8.8 ASA1(config-group-policy)# webvpn ASA1(config-group-webvpn)# anyconnect proceed-installer installed ASA1(config-grouping-webvpn)# anyconnect ask none default anyconnect ASA1(config-group-webvpn)# anyconnect dpd-interval client xxx ASA1(config-group-webvpn)# exit In that location's quite some stuff in the grouping policy, let me break information technology down for you:
- The grouping policy is called "ANYCONNECT_POLICY" and information technology's an internal group policy which means that nosotros configure it locally on the ASA. An external group policy could be on a RADIUS server.
- The VPN tunnel protocol is ssl-customer (for anyconnect) and also ssl-clientless (clientless SSL VPN).
- Separate tunneling has been enabled and nosotros refer to the admission-list "SPLIT_TUNNEL" that we just created.
- The DNS server 8.eight.viii.8 will exist assigned to remote VPN users.
- Normally when the remote VPN user terminates the session, the anyconnect installer volition be uninstalled. The anyconnect proceed-installer installed command leaves it installed on the user'southward calculator.
- The anyconnect ask command specifies how the anyconnect customer will be installed on the user's computer. The none default anyconnect part tells the ASA not to ask the user if he/she wants to utilize WebVPN or anyconnect but just starts the download of the anyconnect customer automatically.
- The anyconnect dpd-interval control is used for Dead Peer Detection. The remote user's anyconnect client volition bank check every 30 seconds if the ASA is still responding or not. You can also use dpd-interval gateway then that the ASA checks if the remote user is still responding.
After the group policy configuration we have to create a tunnel grouping which binds the grouping policy and VPN pool together:
ASA1(config)# tunnel-group MY_TUNNEL type remote-access ASA1(config)# tunnel-group MY_TUNNEL general-attributes ASA1(config-tunnel-general)# default-group-policy ANYCONNECT_POLICY ASA1(config-tunnel-general)# address-pool VPN_POOL ASA1(config-tunnel-general)# exit When the remote user connects, the ASA will bear witness a grouping name to the remote user, nosotros tin specify the group proper noun like this:
ASA1(config)# tunnel-group MY_TUNNEL webvpn-attributes ASA1(config-tunnel-webvpn)# grouping-alias SSL_USERS enable Y'all volition encounter that when the remote user connects, the ASA will show the group proper noun "SSL_USERS". If you accept multiple tunnel groups so your remote users should be able to select a certain tunnel group:
ASA1(config)# webvpn ASA1(config-webvpn)# tunnel-group-list enable Now we can create a user account:
ASA1(config)# username SSL_USER password MY_PASSWORD We demand to tell the ASA that this user business relationship is allowed to access the network:
ASA1(config)# username SSL_USER attributes ASA1(config-username)# service-blazon remote-access Everything is now in place on the ASA. We tin use the client to connect to the ASA and install the anyconnect customer.
Client Configuration
I will employ a Windows vii client with Cyberspace Explorer for this. Start the browser and enter the IP address of the ASA as the URL. If y'all utilise HTTP, y'all will be redirected to HTTPS:
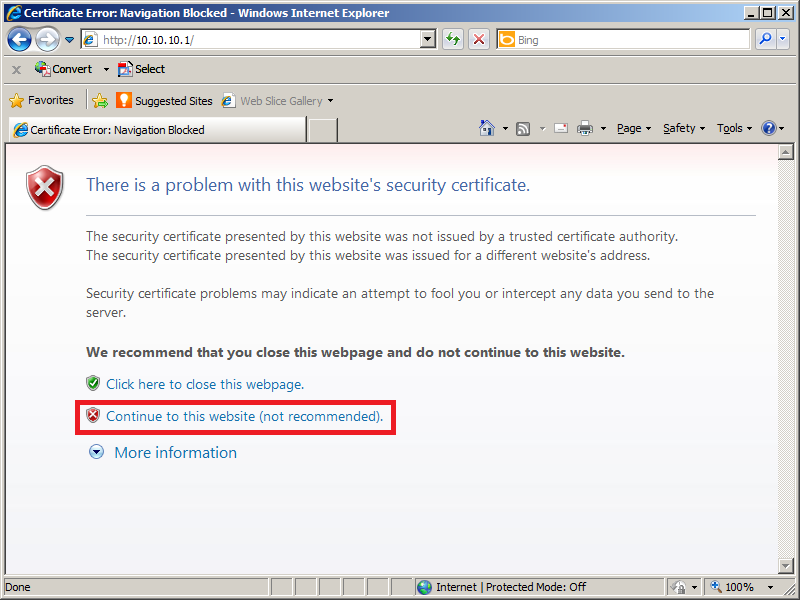
The ASA is using a cocky-signed certificate that is not recognized by the browser and then that's why y'all see this error. Click continue and yous will see the following screen:
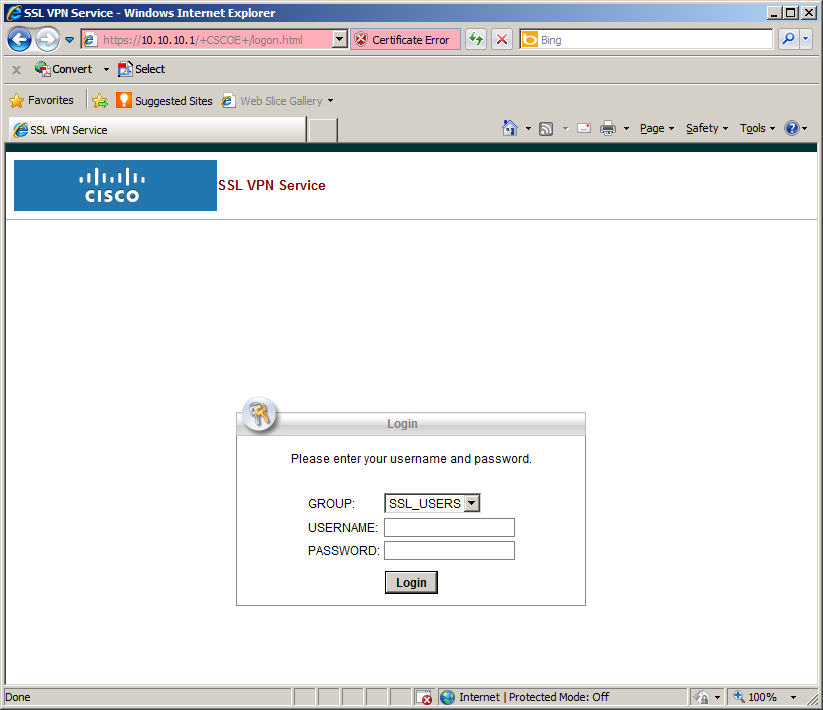
Now you can authenticate yourself. Enter the username and password that we created before. The group proper noun is the group alias that nosotros created. Once y'all are authenticated yous volition run across this:
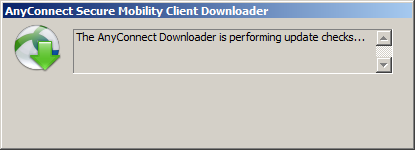
The client tries to download the Anyconnect automatically, this is because of the anyconnect ask none default anyconnect command that nosotros used. Since we are using a self-signed document you volition become the following fault bulletin:
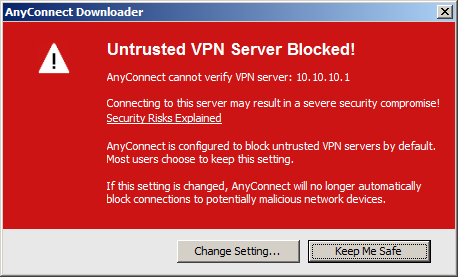
You need to click on the Change Setting push and y'all will see this:
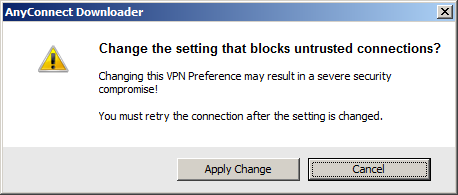
Click on the Apply Change button and you volition meet this:
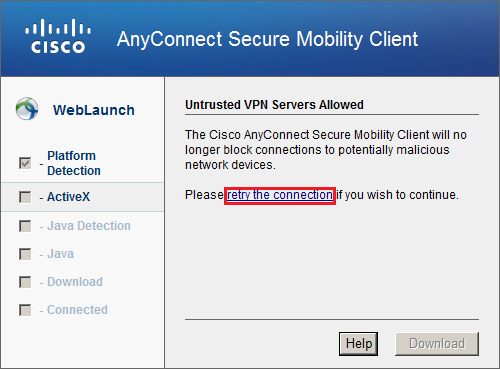
Click on the retry the connection link and you will run into this:
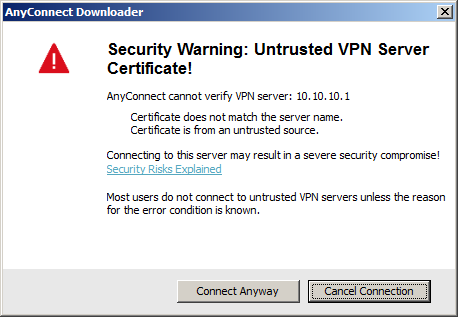
We go one more warning that the certificate cannot be verified. Click on Connect Anyhow and the download volition finally start:
Once it is completed you lot will see this:
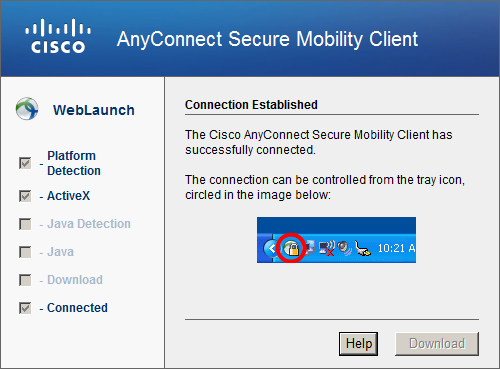
The Anyconnect customer has been installed and the connection has been established. If you look in the Windows taskbar then yous will observe a small icon:
![]()
Click on information technology and it will open the Anyconnect customer, hither's what it looks like:
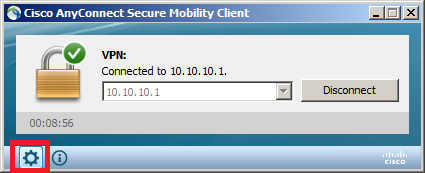
It is connected and if you want to see some details you need to click on the trivial "gear" icon, it will give you a nice overview of the connection:
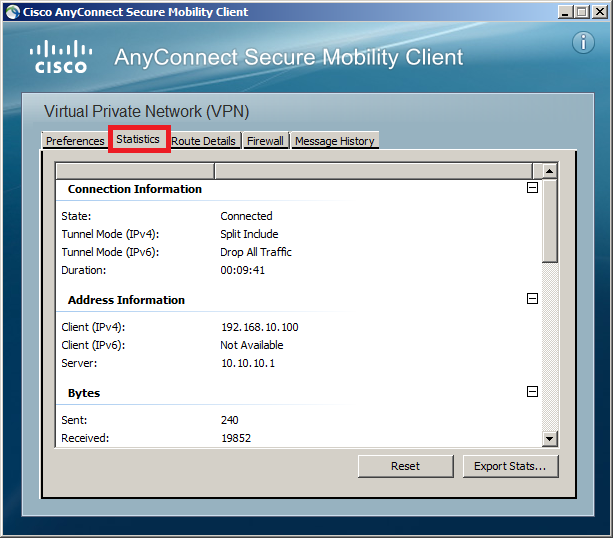
This shows you the IP address that the client has received and some statistics about how much bytes were sent/received. This is looking good merely it's important to verify a couple of things before we cease this lesson…
We got a lot of messages nigh the self-signed document that is untrusted. For this instance it doesn't matter but in a production network it might be a good idea to gear up this problem. In another lesson I will show you how to use certificates that are trusted past your user's browser.
Verification
Client Verification
First we'll generate some traffic on the customer, run into if it can reach R1 on the inside network:
C:UsersVPN>ping 192.168.ane.1 Pinging 192.168.1.1 with 32 bytes of information: Reply from 192.168.1.i: bytes=32 time=2ms TTL=255 Answer from 192.168.one.i: bytes=32 fourth dimension=2ms TTL=255 Reply from 192.168.1.1: bytes=32 time=2ms TTL=255 Reply from 192.168.i.one: bytes=32 fourth dimension=2ms TTL=255 Ping statistics for 192.168.one.1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 2ms, Maximum = 2ms, Average = 2ms That'southward looking good, let'southward use ipconfig to see what IP accost it has received:
C:UsersVPN>ipconfig /all Windows IP Configuration Host Name . . . . . . . . . . . . : VPN-PC Primary Dns Suffix . . . . . . . : Node Type . . . . . . . . . . . . : Hybrid IP Routing Enabled. . . . . . . . : No WINS Proxy Enabled. . . . . . . . : No Ethernet adapter Local Area Connection three: Connectedness-specific DNS Suffix . : Clarification . . . . . . . . . . . : Cisco AnyConnect Secure Mobility Client Virtual Miniport Adapter for Windows x64 Concrete Address. . . . . . . . . : 00-05-9A-3C-7A-00 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.10.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : DNS Servers . . . . . . . . . . . : 8.8.8.viii NetBIOS over Tcpip. . . . . . . . : Enabled You tin can see that we received IP address 192.168.ten.100 (the starting time IP accost from the VPN pool). Anyconnect creates an additional interface, but like the legacy Cisco VPN customer does.
ASA Verification
Everything on the client was looking good, in that location's as well a useful control on the ASA to verify our piece of work:
ASA1# evidence vpn-sessiondb anyconnect Session Blazon: AnyConnect Username : SSL_USER Index : half-dozen Assigned IP : 192.168.10.100 Public IP : x.10.10.two Protocol : Clientless SSL-Tunnel DTLS-Tunnel License : AnyConnect Premium Encryption : Clientless: (1)RC4 SSL-Tunnel: (1)RC4 DTLS-Tunnel: (ane)AES128 Hashing : Clientless: (1)SHA1 SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1 Bytes Tx : 6252805 Bytes Rx : 133830 Group Policy : ANYCONNECT_POLICY Tunnel Group : MY_TUNNEL Login Time : 16:30:35 UTC Tue Dec 9 2014 Duration : 0h:11m:28s Inactivity : 0h:00m:00s NAC Consequence : Unknown VLAN Mapping : Northward/A VLAN : none This shows us that user "SSL_USER" is connect, the IP accost information technology has received and also that information technology is using a SSL tunnel…mission accomplished! I hope this lesson has been useful to learn about remote access VPN using the Anyconnect client. If you lot take whatsoever questions, experience free to go out a annotate!
DOWNLOAD HERE
Posted by: frisktwoultaidne1975.blogspot.com

0 Comments